+46 73 505 02 52
info@ensec.se
Features
- High update rate, 2000-3000 MHz per second
- Frequency range 9 kHz – 6000 MHz
- Reaction time: 2-3 seconds
- Instantly detects digital signals with short bursts
- Can detect and locate the transmitter simultaneously
- Quickly and reliably detects all kinds of RF listening devices, including analog, digital, constantly existing and intermittent, sending audio or video, with or without encryption
- Finds hidden surveillance devices employing the digital standards GSM, 3G, 4G/LTE, 5G(<6GHz), Bluetooth, Wi-Fi, DECT, etc.
- Detects illegal information transmission in AC, telephone, Ethernet, alarm and other wires as well as in the infrared range with the help of the supplied Multifunction Probe
- Can work in instant detection mode, guarding mode, locating mode and car tracker detection
- Has a 20-50 times higher sensitivity and detection distance compared to conventional RF detectors and near-field receivers
- Can monitor the RF environment 24 hours a day with data logging
- Capable of detecting covert bugging devices with an accumulation function and transmitters hidden within the spectrums of other signals
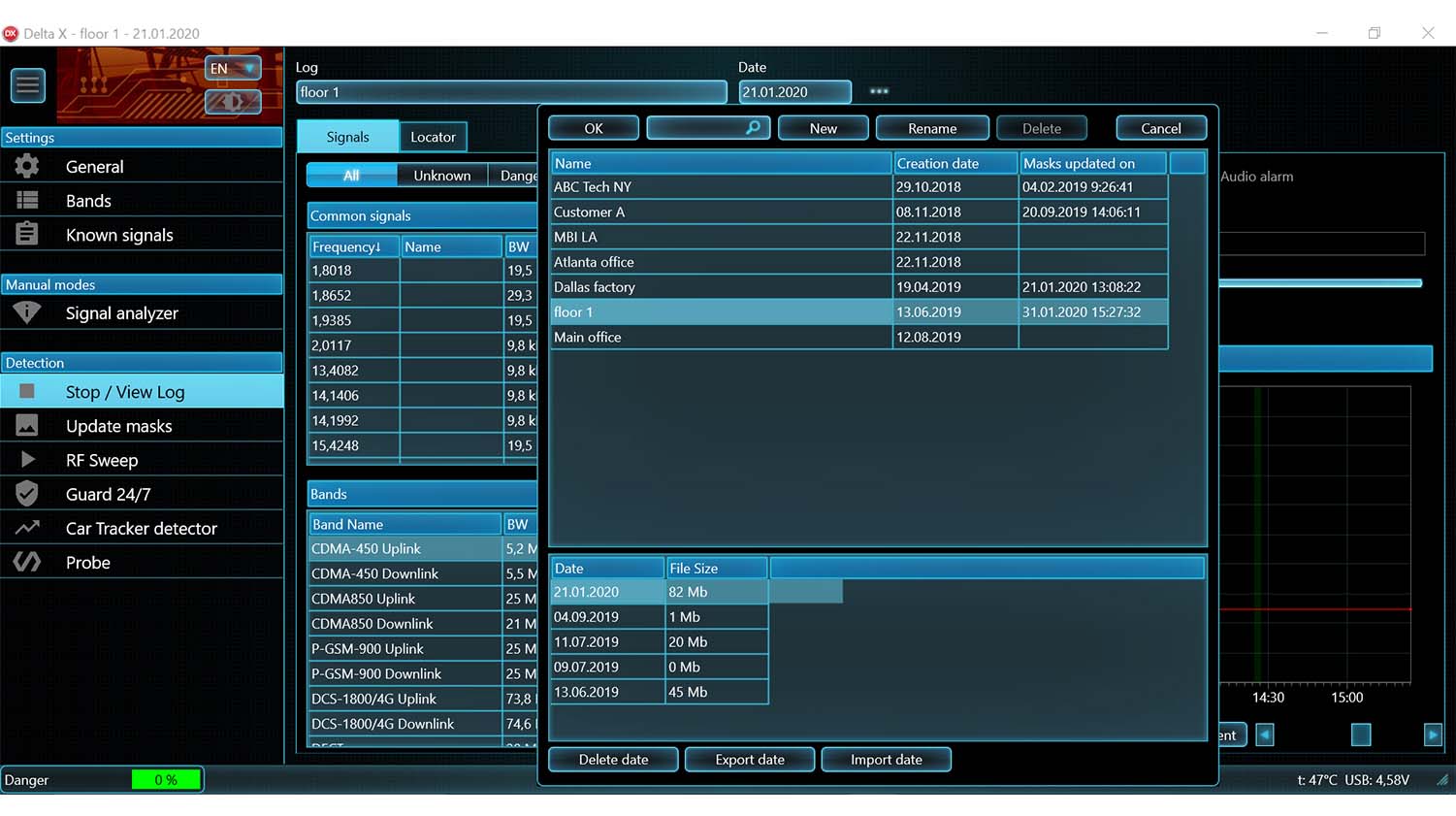
- Supports storage of an unlimited quantity of signals. Full information is stored in the log and can be reviewed during the detection, or at a later time. Multiple logs are supported.
- Demodulation of audio in FM, AM, USB, LSB, CW (adjustable BW 3…240 kHz)
- Alarm relay output can activate external devices when a dangerous signal is detected (turn on a CCTV system, for example)
- Comes in a protected case that allows you to place a 13-14” laptop inside (not included in the supplied set)
- Powered from the laptop’s USB
New features available in the latest updates
- Updated “Alarms” graph can now render two graphs simultaneously: general alarms, and the signal’s alarms.
- The Generate Report feature allows the operator to export the results of detection into a PDF file. The report fully describes the RF environment in the monitored zone by listing dangerous and non-dangerous signals and shows their activity in graphs “Alarms”, “Spectrogram”, “Waterfall” and “Persistence”. Example of report
- Sending alerts by email makes it possible to send notifications about detecting dangerous signals. The alerting message will contain information about the detected signals in the attached PDF report.
- The “Check for updates” button has been added. It can check if a newer version is available and download it.
- Remote access from Windows, iOS or Android. The method of remote access is described now.
Report-Delta-X-detailed-features
Advantages
What it is: a portable system controlled by a laptop computer
- The high capacity of a laptop’s hard drive enables full data logging during the detection (24/7 possible)
- Wider screen is more convenient for analysis
- Compatible with touch screen laptops
- The handheld use of antennas is more convenient for locating transmitters in hard to access places
Handling of the mobile and wireless bands GSM, CDMA, 3G, 4G/LTE, 5G(<6GHz), DECT, Wi-Fi, Bluetooth, etc.
- Mobile and wireless signals are detected simultaneously with analog transmissions
- Mobile/wireless signals are detected with the use of individual thresholds and are displayed separately from other signals
- Activities within each band are stored as one signal with a certain danger level to avoid excessive records in the Signals table and to locate the sources with a hopping frequency
- Additional sweepings on the “short-burst” bands are performed to increase the probability of interception of such signals as GSM, 3G, 4G, DECT, Wi-Fi, Bluetooth, etc.
- External interference from neighboring mobile phones and Wi-Fi routers can be rejected with the help of the thresholds
- The supplied data files allow the operator to adjust the system to the mobile/wireless bands employed in the country of use
Sensitivity and detection distance
- The built-in spectrum analyzer has 20-50 times higher sensitivity and detection distance compared to conventional RF detectors and near-field receivers
- Resistant to interference – sensitivity remains high regardless of the proximity to wireless routers, cordless phones, mobile phones, TV towers, radio broadcasting and mobile communications
Support of the “Known signals” table
- The operator can easily distinguish between safe and dangerous signals
- The TV frequencies employed in the country of use can be quickly imported from the supplied data files
- The FM, VHF/UHF police and municipal channels can be collected and stored for further us
Advanced signal recognition method
- The signals are automatically recognized in the spectrum traces and inserted or updated in the Signals table
- Both analogue and digital signals are captured with an assigning of a corresponding Danger level
Unique algorithm of measuring the signal’s Danger level
- Uses a combination of the reference trace and individual thresholds for mobile/wireless bands
- Takes into consideration both the signal’s strength and bandwidth
- Works for both analogue and digital signals including transmissions with a changing frequency
- Is used during the locating procedure and provides more reliable results compared to the traditional “signal strength” method.
Low demands on the operator’s level of knowledge
- The system can be prepared for detection with the help of the “Update Masks” procedure within a few minutes
- Manual handing of spectrum traces is not necessary
- Everything is done automatically after the detection starts
- The operator is warned by an audio alarm when a dangerous signal is detected
Data logging
- All the spectrum traces and alarms are logged during detection
- The situation at any given time can be reviewed and studied
- 24 hours a day logging provides detection of periodically working/remotely controlled bugging devices
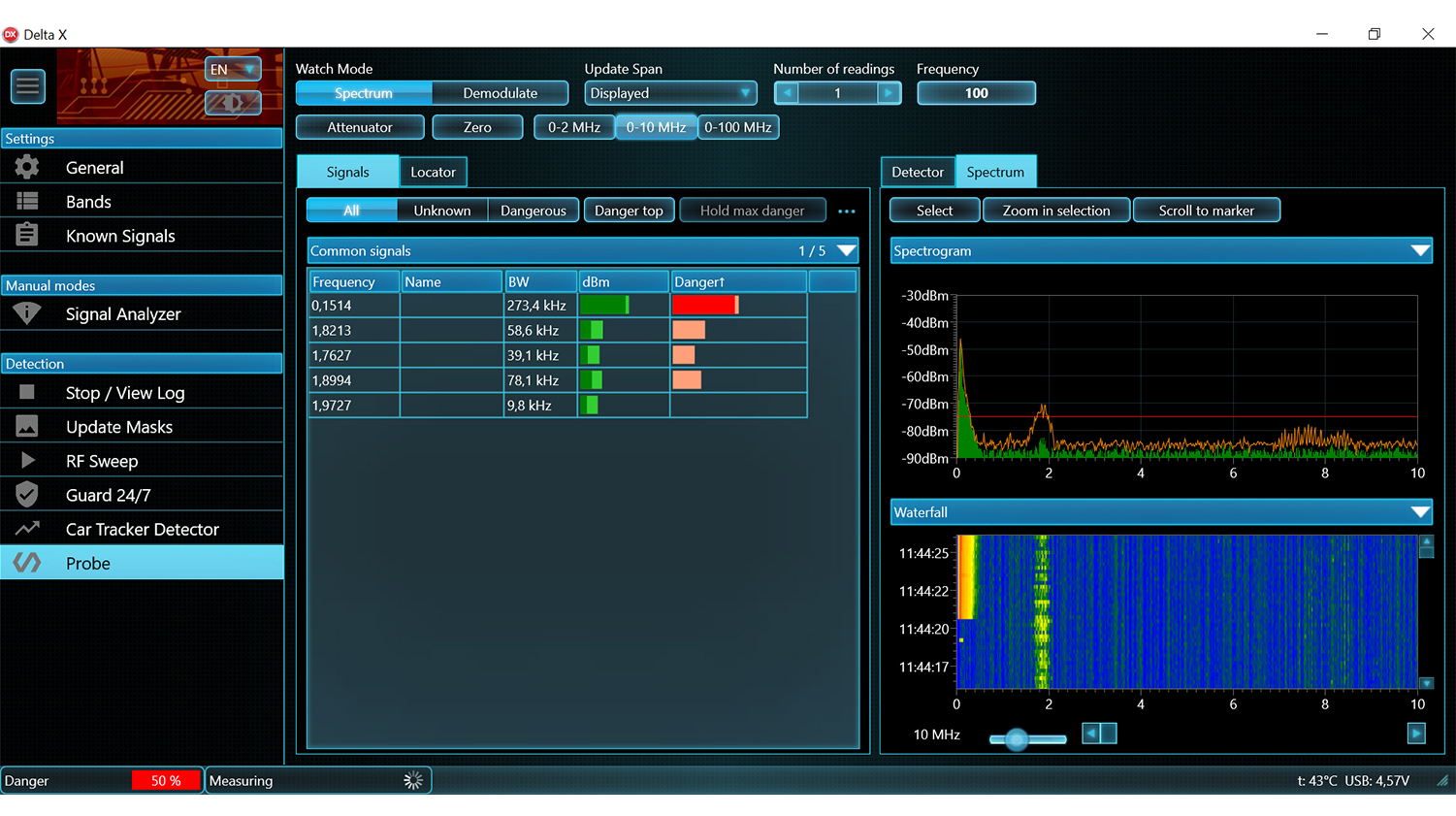
Tracking of the signal’s activity
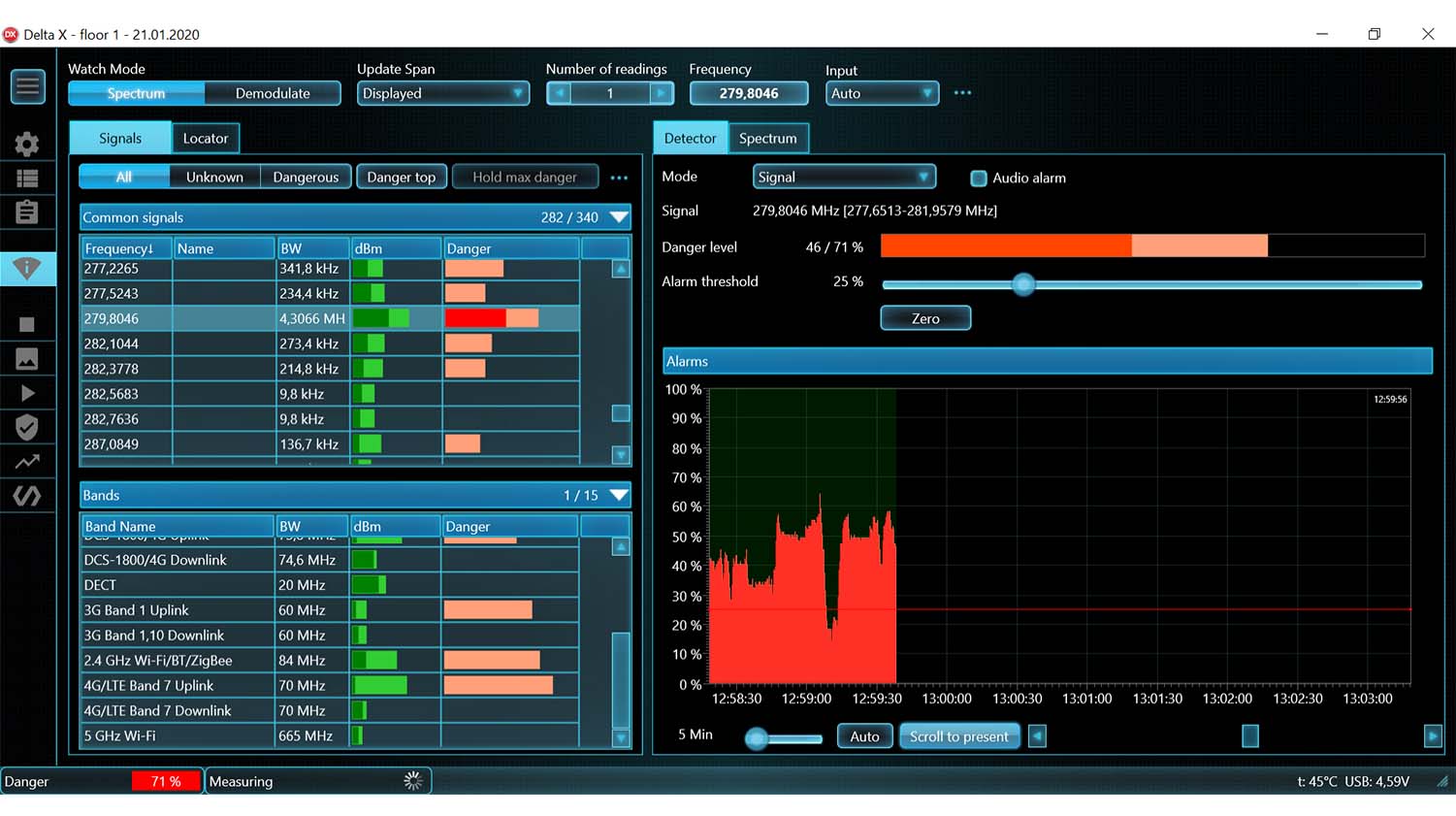
- The full history of each separate signal, or of all signals simultaneously, is displayed on the Alarms graph
- The events at any given time can be reviewed by simply clicking on the graph
- The operator can see the duration of an activity and as such distinguish between any interference and real danger
The Waterfall and Persistence graphs
- Both the present and previous measurements at any given time can be displayed
- The displayed time interval (density) is selectable in the range of 2 minutes to 6 hours
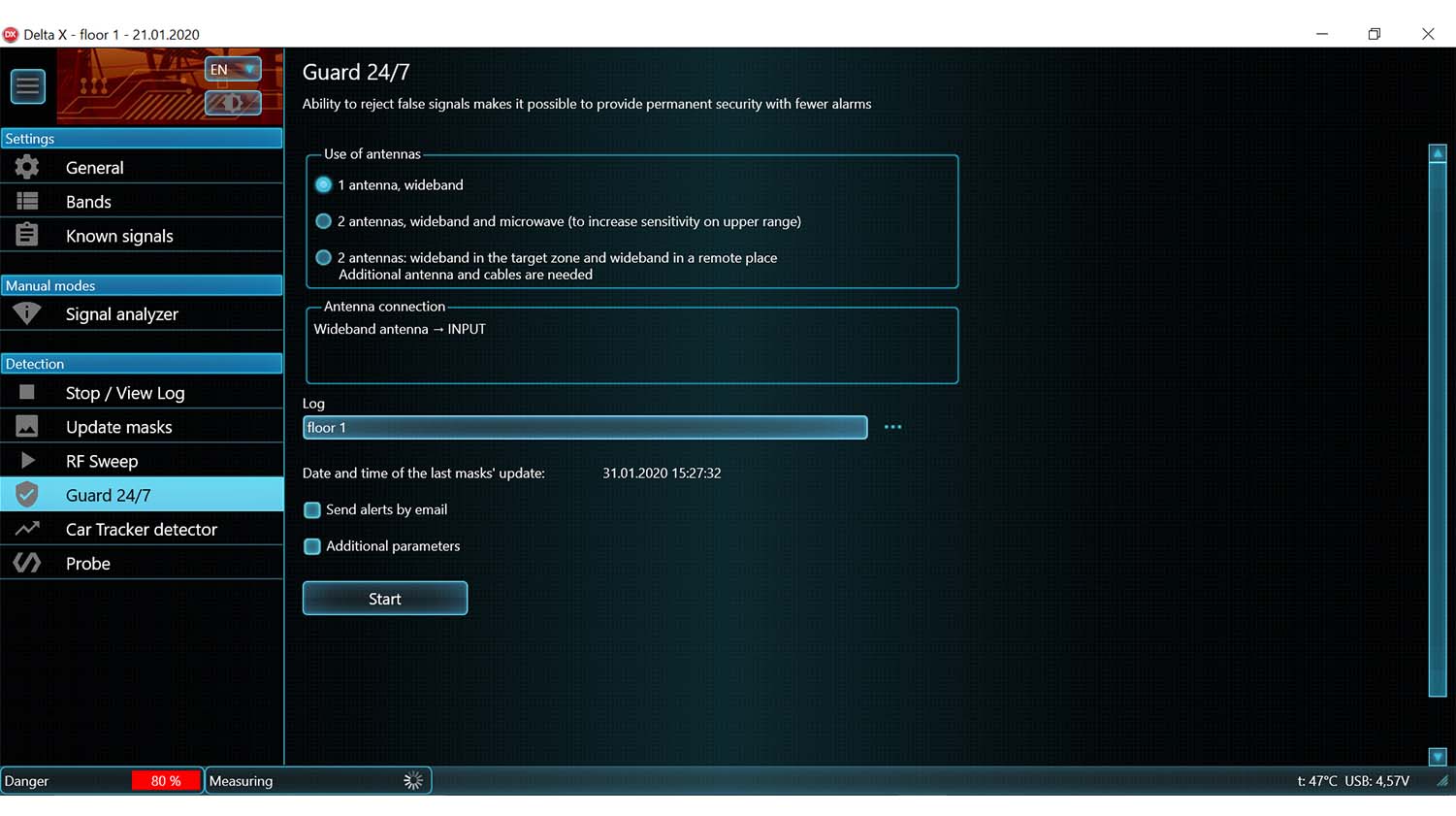
Car Tracker Detector mode
- The monitoring of mobile bands can detect signals from GPS trackers hidden within a vehicle
Specification
- Update rate: 2000-3000 MHz/sec
- Frequency range: 9 kHz – 6000 MHz
- Time of detection (Minimal time of signal’s existence needed for its detection): 2-3 sec
- Spectrum resolution: 9.8 kHz
- Occupied disk space per 24 hours: 12 Gb
- Temperature Range: 0°C to +65°C
- Demands on computer (not included in the supplied set): 3rd gen. or newer Intel dual/quad Core i-series; 1 x USB 3.0; 2 x USB 2.0; Windows 7, 8 , 10
- Displayed dynamic range: -90…-10 dBm
- Displayed spectrum spans: 0.5, 1, 2, 5, 10, 25, 50, 100, 200, 500, 1000, 2000, 3000, 6000 MHz
- Spectrum graphs: Spectrogram, Waterfall
- Spectrogram’s displayed data: Persistence, Live, Max, Threshold
- Detector’s modes: Wide-Range, Signal, Selection
- Updated spectrum span: RF Sweep, Guard 24/7: broadband Signal Analyzer: displayed, selected, real-time Car Tracker Detector: mobile bands
- Fields of ‘Signals’ table: Frequency, Bandwidth, Name, dbm Level, dbm Peak Level, Danger Level, Peak Danger Level
- Fields of ‘Bands’ table:Begin, End, Name, Type, Threshold, Priority, Tracker detection
- Fields of ‘Known Signals’ table: Frequency, BW, Name, Modulation
Functions of the software
- Rich visual representation: Spectrogram/Persistence, Waterfall, Alarms graph
- The Known Signals table allows the system to reject TV, FM and other “friendly” signals while maintaining high sensitivity to unknown signals.
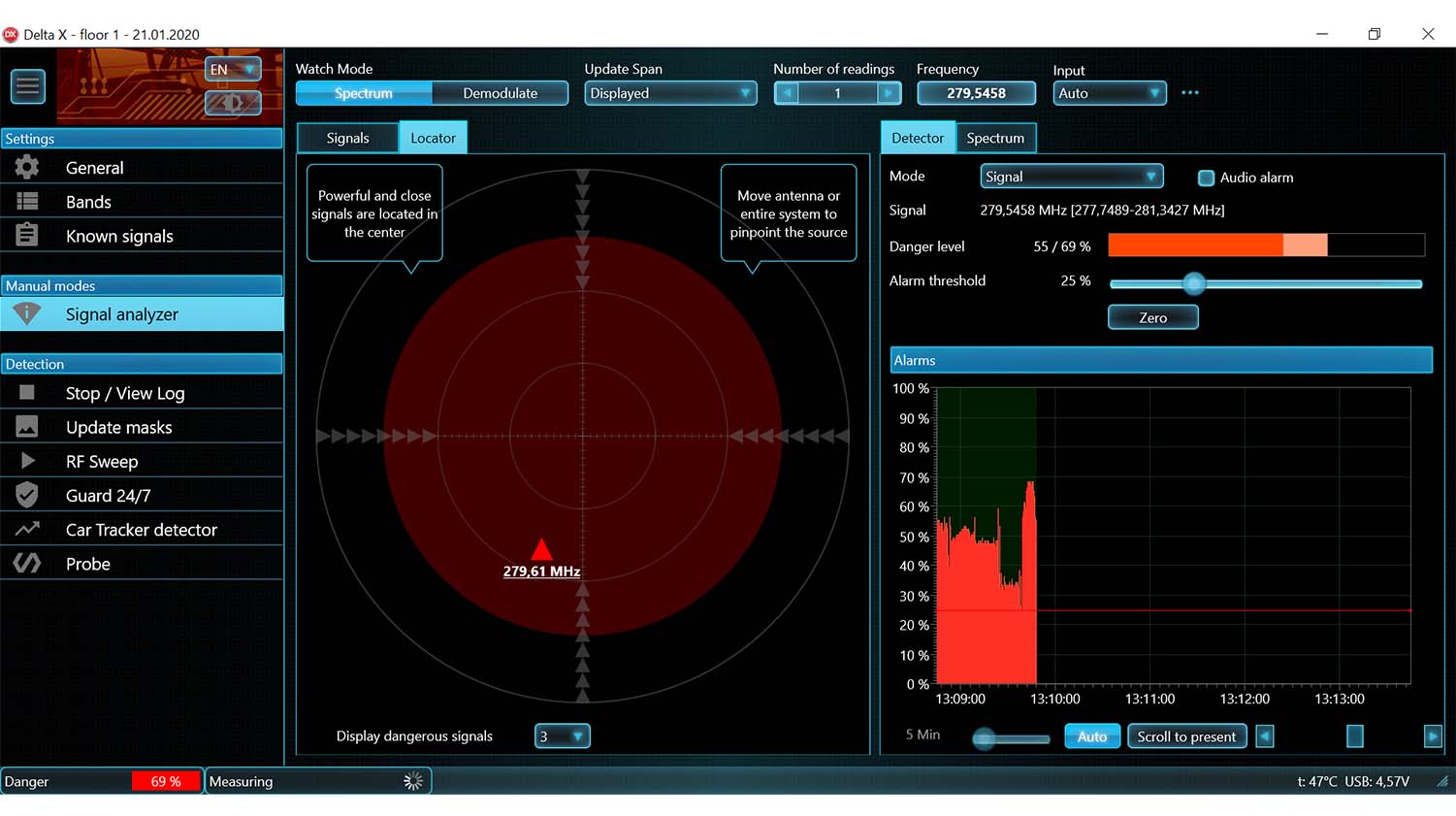
- The Detector and Locator allow the operator to perform location of a bugging device with both visual and audio notification
- The Alarm Threshold decreases the false alarm rate
- The Hold Max Danger feature selects and shows the strongest signals for their location as the system is moved during detection
- The Update Mask procedure allows the operator to quickly adjust the system to the local RF environment in order to reject safe signals
- Sorting and filtering is supported in the Signals table
- The Report function allows the operator to export all obtained information about the desired signals
- Is easily localizable to any language
Working modes
- Stop/View Log
Review of the detection results stored in the log. The Signals table, Spectrogram, Waterfall and Alarms graph give full information about the detected signals and alarm events - Update masks
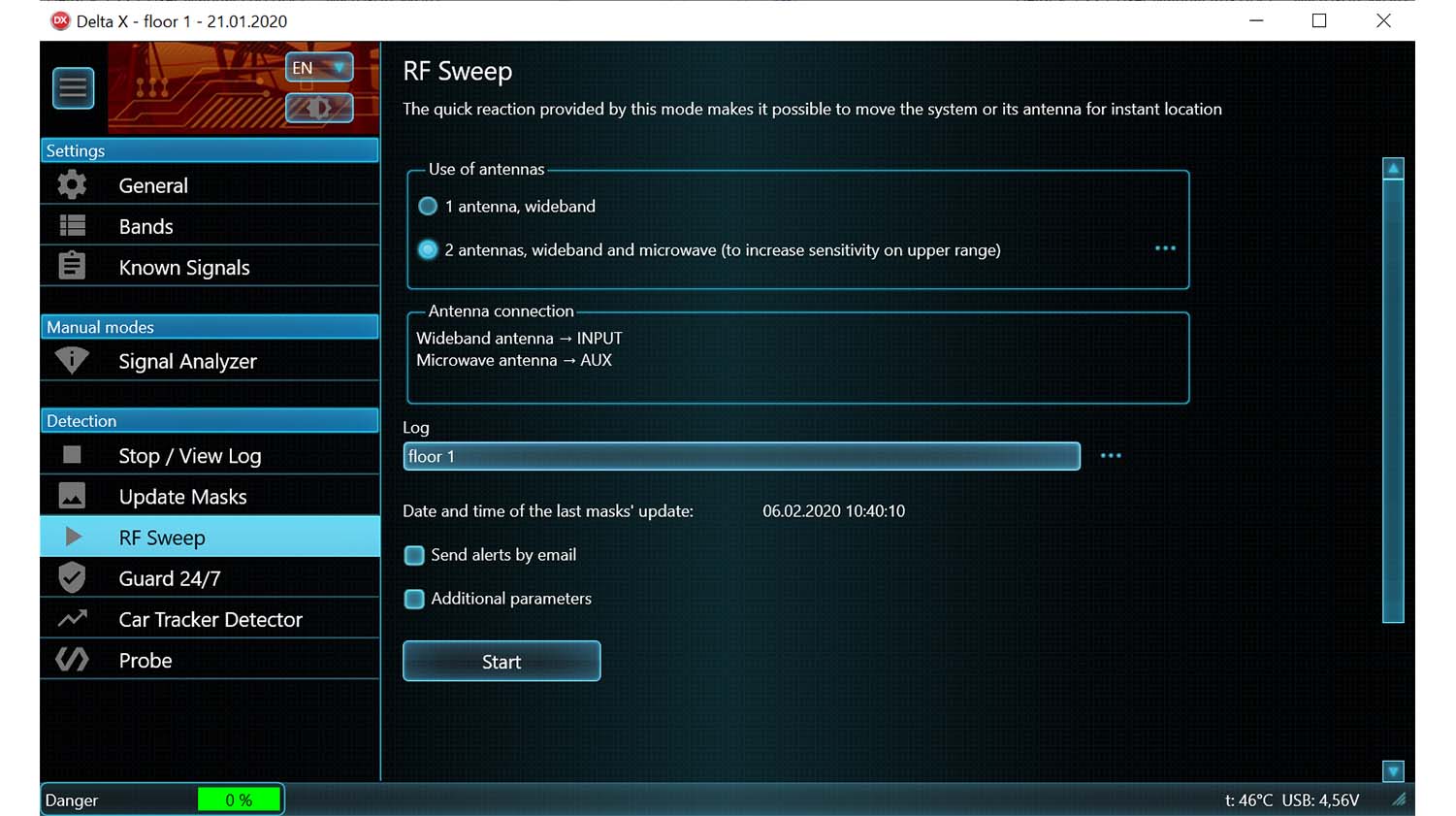
Quick preparation for detection – the system automatically accumulates the broadcasting and other safe signals existing in the area in order to pass over them during the subsequent detection - RF Sweep
The main detection mode. Provides maximum reaction time and the highest sensitivity. The operator can move the system or its antenna during the detection. - Guard 24/7
Rejection of short transmissions and usage of two antennas reduces false alarms in this mode. Suitable for 24 hour detection without unwanted false alarms - Car Tracker Detector
Detection of vehicle mounted GPS trackers transmitting the coordinates via mobile networks - Probe
Checking of AC, Ethernet, Telephone and Alarm wires and the infrared/low frequency for the presence of unwanted bugging signals - Signal Analyzer
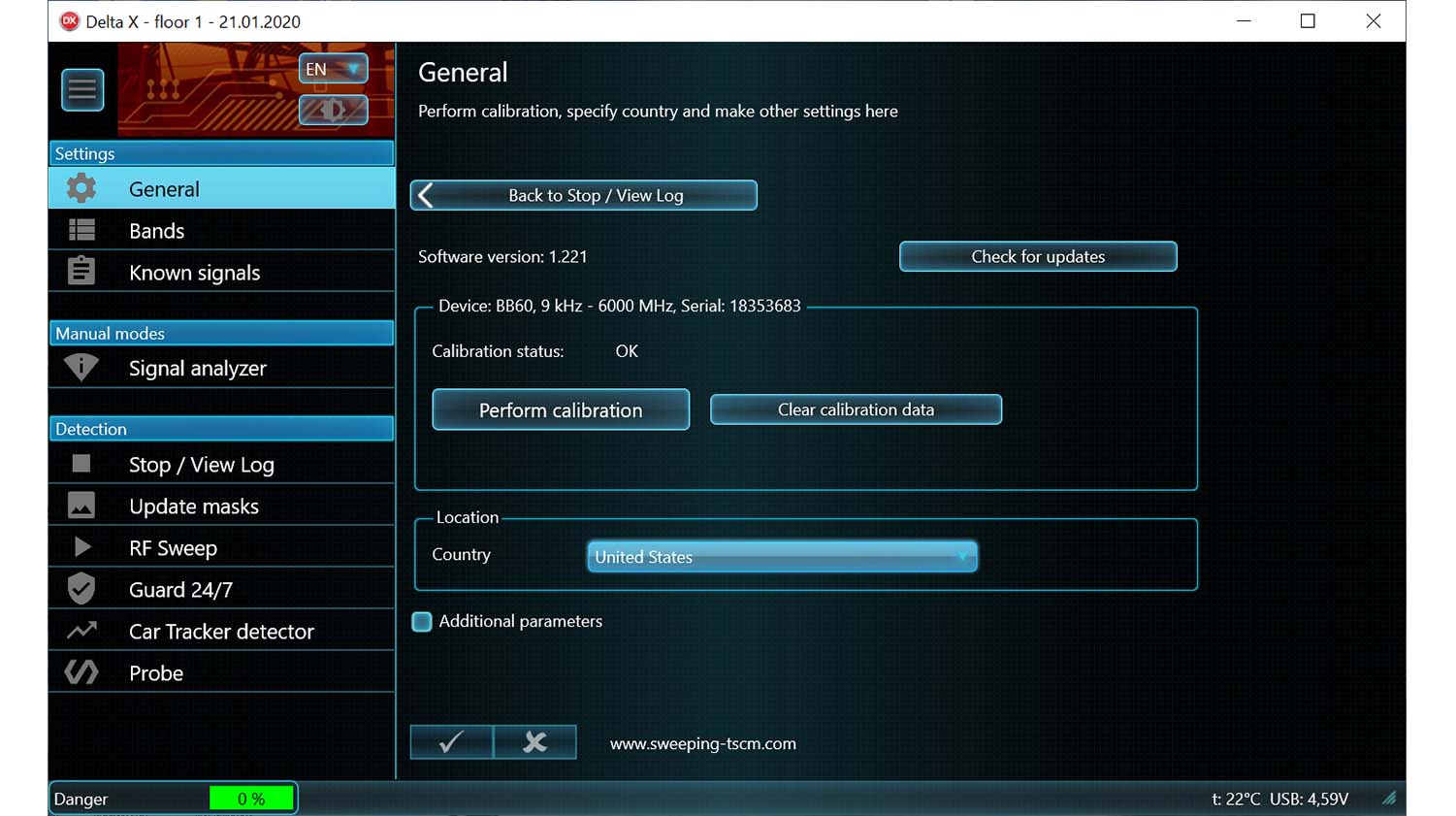
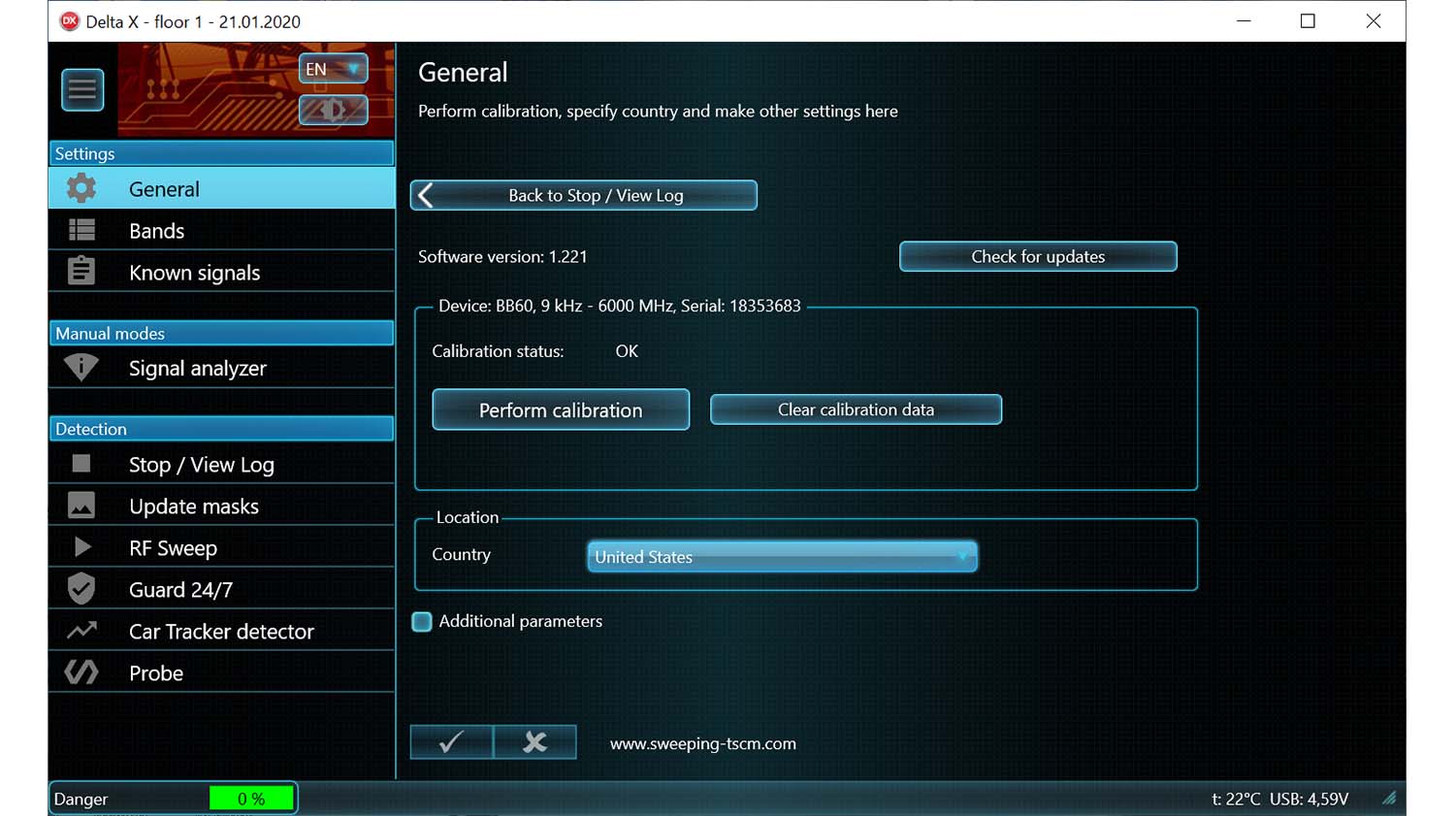
Analysis, demodulation and physical locating of detected signals - Settings
Includes the general settings and information about the mobile networks and wireless bands existing in the area as well as the known signals table
Supplied set
- Main unit with the built-in spectrum analyzer and RF switcher
- Software Delta X on the USB flash memory
- ODA-4 – omnidirectional wideband antenna
- MWA-6 – microwave antenna
- Multifunction Probe with cables
- Coaxial low-attenuation cable 5 m
- In-line modular adapter
- Tripod convertible to handle
- Set of accessories (case’s cover lock, angle USB adapters, BNC-to-SMA and SMA-to-BNC adapters)
Supplied set
- Main unit with the built-in spectrum analyzer and RF switcher
- Software Delta X on the USB flash memory
- ODA-4 – omnidirectional wideband antenna
- MWA-6 – microwave antenna
- Multifunction Probe with cables
- Coaxial low-attenuation cable 5 m
- In-line modular adapter
- Tripod convertible to handle
- Set of accessories (case’s cover lock, angle USB adapters, BNC-to-SMA and SMA-to-BNC adapters)